Release 1.11.3
Release Date: 03/05/2024
Features
Support for Multiple Certificates on SAML Authentication
You are now able to configure multiple certificates for SAML authentication by configuring in the same configuration property multiple certificates separated by commas.
Improved monitor page
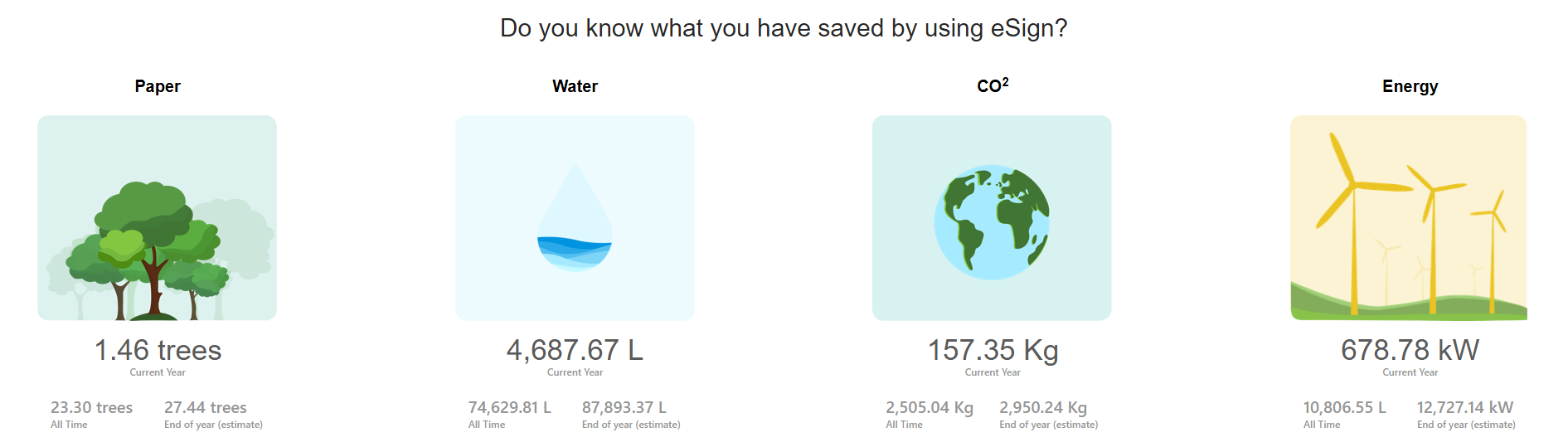
Improved sustainability data, compare current year with all time data and end of year prediction.
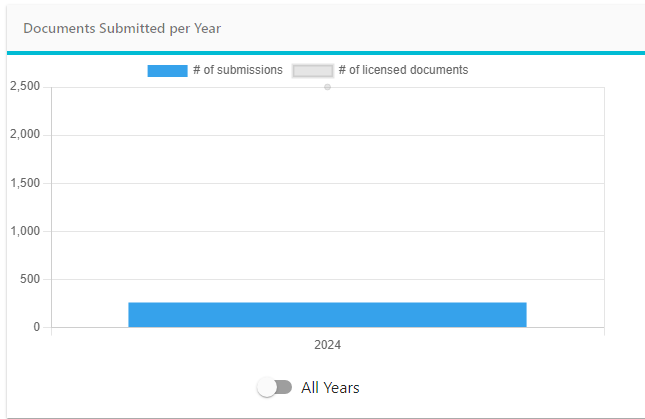
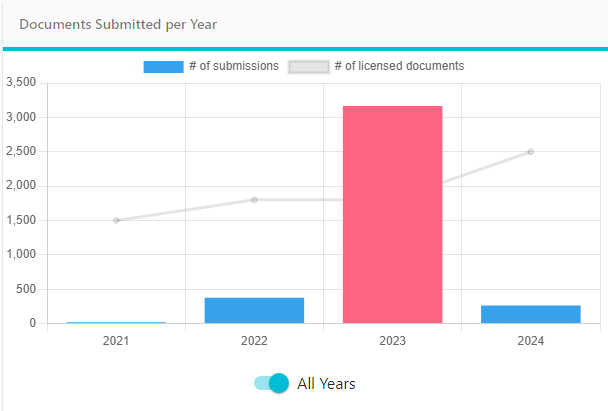
Improved Documents Submitted per Year graphic with a button to switch between current year and all time data.
|
|
Features
-
Added better logs with corresponding request ids to external service dependent signatures (e.g. Multicert’s Sign&Stash).
-
Improved bulk/external signature process by adding a new 'PENDING_RESPONSE' state that informs that the external service is still processing the request.
-
Document locks have been introduced in finalizing signatures (the ones done after the document is submitted). "artifact.sign.finalize.lock," has been introduced, with its default setting configured to true. Consequently, if the desired behavior is to avoid this locking mechanism, it can be altered by setting the property to false.
Fixes
-
Fixed a bug where addin exceptions would be supressed. This caused the addins to not properly log errors.
-
Fixed a bug in Sign&Stash signature’s validation that could throw an exception improperly invalidating the signature and cancelling the operation.
-
Fixed a bug in jobs that caused an error (and job cancelation) due to improper handling of document’s custom properties.
-
Fixed a bug that caused the submitted documents service (analytics) to report wrong contracted numbers when there were multiple licenses for the same time period.
-
Fixed a bug with some Oracle database versions where the registering of bulk audit data would fail due to improper blob comparison.
-
Fixed a bug with some Oracle database versions where the comparison of truststore certificates would fail due to improper blob comparison.
-
CRL cache overhaul fixed various CRL validation issues.
-
Fixed a bug where embedded CRLs were not properly validated.
-
Fixed signature methods to follow the same order as version 1.10
-
Fixed a bug where some configuration property values had out of date 'modified_by' and 'last_modified' fields.
-
Fixed a bug where some analytic entries (bulk actions only) would not have the 'document_type' field set.
Security Vulnerabilities
Fixed vulnerabilities
| Dependency | Severity | Vulnerability |
|---|---|---|
jackson-databind |
CVE-2023-35116 |
"The vendor’s perspective is that the product is not intended for use with untrusted input." |
h2 |
CVE-2022-45868 |
These vulnerabilities only affect H2 databases, which are intended for demo purposes only and should not be used in production environments |
bcprov-jdk15on |
CVE-2023-33201 |
This vulnerability only affects integrations with LDAP CertStore, which is out of the scope of eSign |
Whitelisted vulnerabilities
| Dependency | Vulnerability | Description |
|---|---|---|
h2 |
CVE-2018-14335 |
These vulnerabilities only affect H2 databases, which are intended for demo purposes only and should not be used in production environments |
itext-core |
CVE-2022-24198 |
iText dismissed this CVE:
"Vendor does not view this as a vulnerability and has not found it to be exploitable." |
jose4j |
CVE-2023-31582 |
This vulnerability does not affect eSign as it does not allow the configuration of the number of hashing iterations (which is set at a safe level). |
quartz |
CVE-2023-39017 |
Quartz functionalities are not exposed to the outside. |
spring-web |
CVE-2016-1000027 |
Spring dismissed this CVE:
"The vendor’s position is that untrusted data is not an intended use case. The product’s behavior will not be changed because some users rely on deserialization of trusted data." |
Upgrade Notes
If upgrading from 1.10.x, check the migration steps to understand how to upgrade.