Release 1.3.1
Release Date: 29/08/2023
| eSign Portal may require additional licensing |
Key features
Added a new way to display partitioned data for the signers and signatures widgets
Both the signers and signatures widgets now have a new way to display partitioned data. This new feature allows you to easily organize information based on percentage values or absolute values. This enhancement significantly improves the readability and simplifies navigation through your analytics data. Enjoy a more immersive and user-friendly experience as you explore your insights.
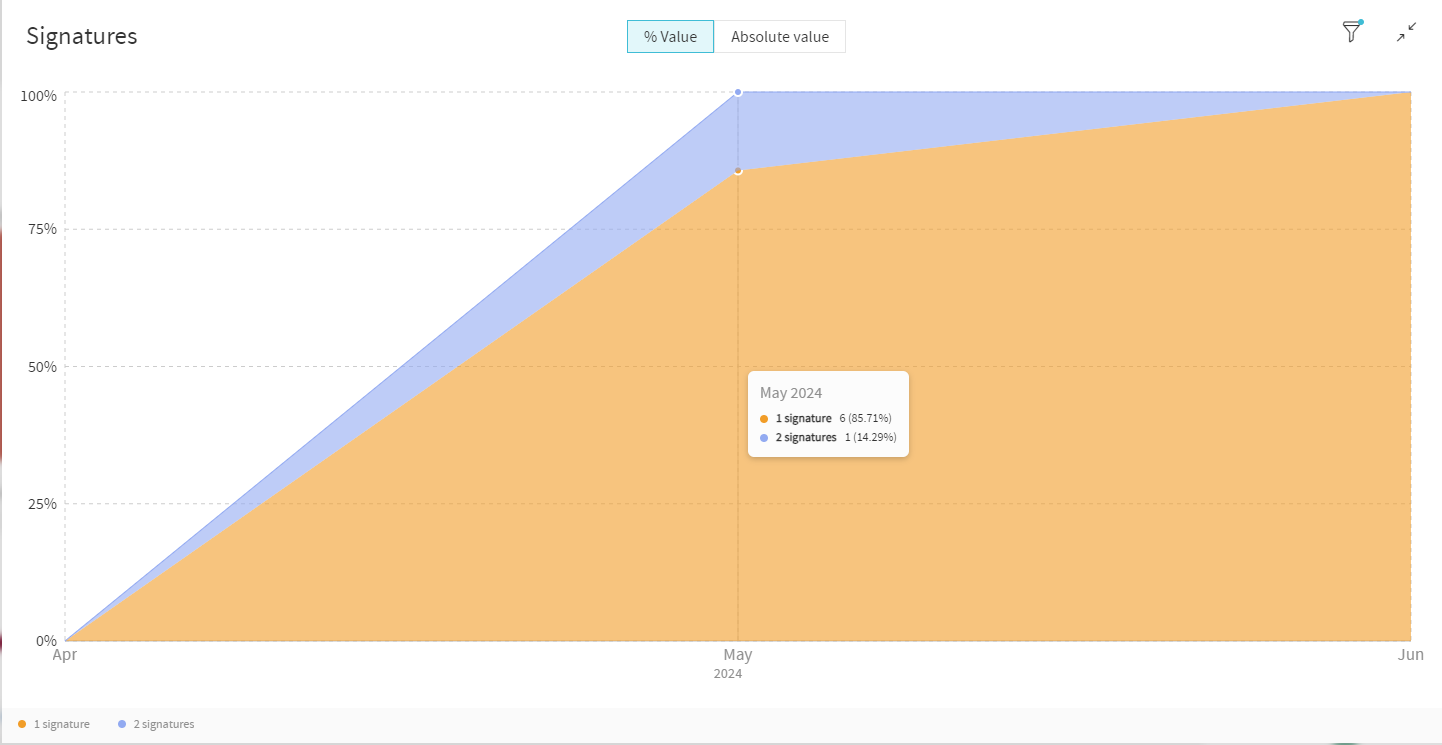
New ui for data partition (Date Separator)
Now when viewing the data partitioned by date, you will see a new separator that makes it easier to distinguish between different time periods. This new feature enhances the readability and usability of the data, allowing you to quickly identify the time frame of each data entry.
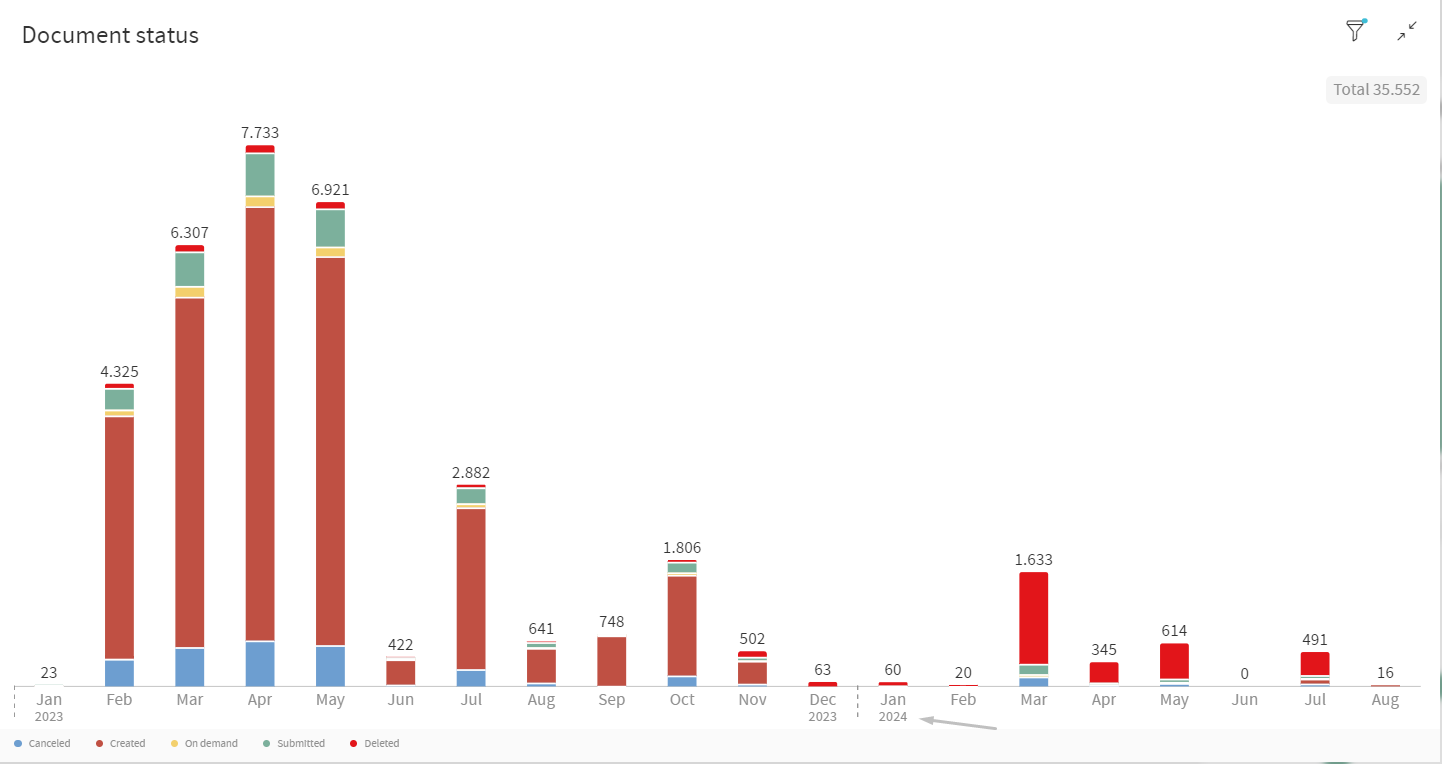
Features
-
Added a new configuration for the data limits
-
Responsive number of entries on bar chart based on the screen size
-
Helm chart now with support for Azure Key Vault
-
Improved Readability and Usability
-
Legends UI upgrades
-
User widget now has a bar chart when only one entry is present
-
New Submitted documents UI
-
New Filters UI
-
New Tooltips
-
New UI for the data pagination
-
Fixes
-
Minor UI fixes
-
Fixed a bug that would show values for dates past the current date
-
Fixed translation issues
-
Fixed performance issues (While resizing the window, the graphs would take a long time to render)
-
Fixed bugs that would in some cases would show NaN values instead of the actual data
-
Fixed widgets crashes when certain filters were applied
-
Fixed a bug on the Signers widget that would show the old data after a new search
-
Fixed a bug with mssql database support
Security Vulnerabilities
Known vulnerabilities
| Dependency | Severity | Vulnerability | Description |
|---|---|---|---|
snakeyaml.jar |
CRITICAL |
CVE-2022-1471 |
SnakeYaml’s Constructor() class does not restrict types which can be instantiated during deserialization. Deserializing yaml content provided by an attacker can lead to remote code execution. |
okio-2.8.0.jar, okio-jvm-3.2.0.jar |
HIGH |
CVE-2023-3635 |
GzipSource does not handle an exception that might be raised when parsing a malformed gzip buffer. |
Whitelisted vulnerabilities
| Dependency | Vulnerability | Description |
|---|---|---|
h2 |
CVE-2022-45868 |
These vulnerabilities only affect H2 databases, which are intended for demo purposes only and should not be used in production environments |
jackson-databind |
CVE-2023-35116 |
"The vendor’s perspective is that the product is not intended for use with untrusted input." |
jetty-http |
CVE-2023-40167 |
At the date of the release the provider had not provided any fix for the vulnerability. |
spring-web |
CVE-2016-1000027 |
Spring dismissed this CVE: "The vendor’s position is that untrusted data is not an intended use case. The product’s behavior will not be changed because some users rely on deserialization of trusted data." |