Hotfix 1.10.5
Release Date: 30/06/2023
Key features
Hide buttons from toolbar
System operators can now configure eSign to hide toolbar icons in eSign Viewer.
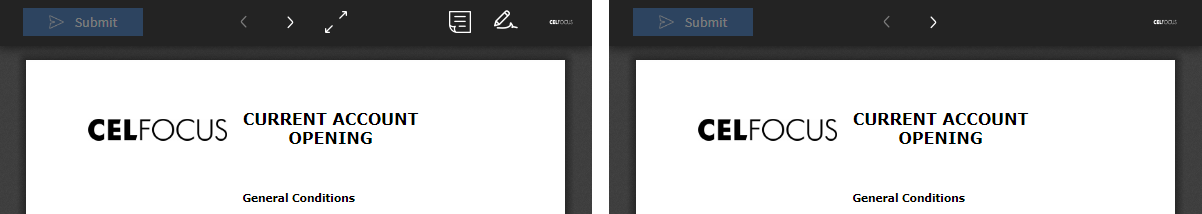
Use property "server.viewer.menubuttons.hidden" to list the identifiers of all buttons to hide.
Annotations displaying user friendly name
It is now possible to configure eSign to display the user’s friendly user in annotations (instead of the username).
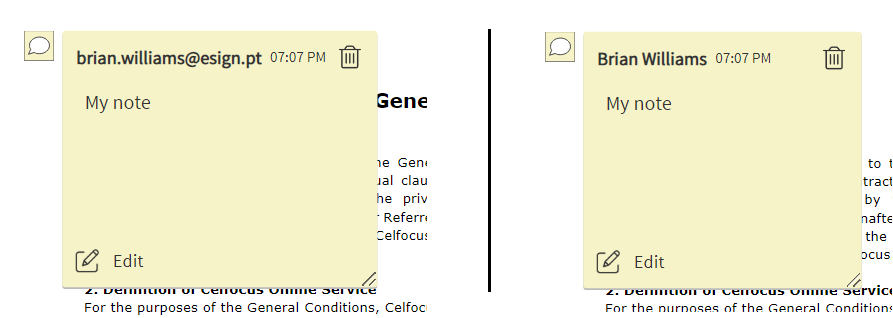
Use property "pdf.annotations.title" switch between the default USERNAME and FRIENDLYNAME.
Disable Annotations per Document
Creating, editing and deleting annotations can now be disabled per document.
When creating a document add, the variable ALLOW_ANNOTATIONS with value true or false (default is false).
Explicit Confirmation on Click to Sign signature
It is now possible to configure eSign to display a confirmation dialog with a user performs a Click to Sign signature.
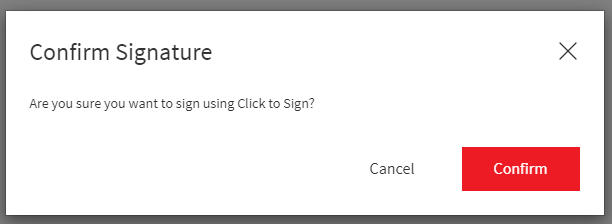
Use property "server.viewer.clicktosign.confirm" with value true or false to determine if a confirmation dialog should be presented (default is false).
Obfuscate sensitive information from Logged requests
Configure a list of sensitive field names that will be obfuscated in the logs displayed in Log Viewer.
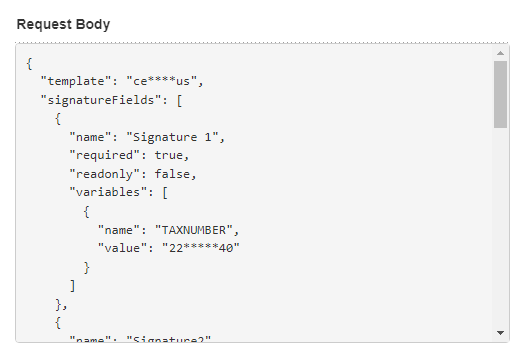
Use property "logging.body.filter" to include the list of sensitive field names.
Partitioning
All Analytics API, control the resulting dataset granularity with partitioning. You can now partition data per Year, Month, Days or Hours.
The following endpoints are now supported by the Analytics V2 API:
-
Signers per document
-
Signatures per document
-
Users per channel
-
Users per channel
| The original API is still supported as the new feature is available at /analytics/v2/ |
Features
-
[ESSD-156] Disable annotations per document
-
[ESSD-169] Display friendly name in annotations
-
[ESSD-188] Prevent uploading documents with attached documents with embedded Javascript
-
[ESSD-200] Explicit confirmation on Click to Sign signatur
-
Hide buttons from the menu bar
-
Obfuscate sensitive information from logs
-
Signers API with support for time partitioning
-
Signatures API with support for time partitioning
-
Channel Volume API with support for time partitioning
-
Analytics queries executed done with explicit NOLOCK
-
eSign docker image updated to use alpine 3.18
Fixes
-
[ESSD-170] Fixed document synchronization issue between server instances for specific document types
-
[ESSD-183] Fixed issue that allowed a named job to be created with special characters and become unmanageable
-
[ESSD-184] Session tokens are no longer logged and displayed in Log Viewer when calling /inspect and /authorization APIs
-
[ESSD-202] Fixed visual bug when rendering comb fields in eSign Viewer
-
[ESSD-204] Fixed visual bug when rendering check boxes of PDF documents that do not fully abide to the PDF standard
-
[ESSD-207] Fixed exception occurring when validating certain documents with signatures with "no policy"
-
Documents upload to eSign that already have annotations no longer render annotations twice in eSign Viewer
-
Fixed uncontrolled exception when adding large audit information via REST API
-
Fixed issue when using Configuration Manager API to upload multiple entries of a configuration with the same value.
-
Fixed exception occurring when attempting to reset a document
-
Fixed issue that causes annotation’s titles to always display the username of the user in session, instead of the name of the user that created the annotation
Security Vulnerabilities
Fixed vulnerabilities
| Dependency | Severity | Vulnerability |
|---|---|---|
guava.jar |
HIGH |
CVE-2023-2976 |
mongo-java-driver.jar |
MEDIUM |
CVE-2021-20328 |
owasp-java-html-sanitizer.jar |
CRITICAL |
CVE-2021-42575 |
spring-core.jar |
CRITICAL |
CVE-2023-20863 |
curl |
HIGH |
CVE-2023-27533, |
Known vulnerabilities
| Dependency | Severity | Vulnerability | Description |
|---|---|---|---|
jackson-databind.jar |
HIGH |
CVE-2023-35116 |
DISPUTED The vendor’s perspective is that the product is not intended for use with untrusted input. |
Whitelist vulnerabilities
| Vulnerability | Description |
|---|---|
CVE-2016-1000027 |
Spring dismissed this CVE: "The vendor’s position is that untrusted data is not an intended use case. The product’s behavior will not be changed because some users rely on deserialization of trusted data." https://nvd.nist.gov/vuln/detail/CVE-2016-1000027 |
CVE-2021-42392 |
These vulnerabilities only affect H2 databases, which are intended for demo purposes only and should not be used in production environments |
CVE-2022-0839 |
This vulnerability does not affect eSign as it does not support external inputs to liquibase libraries |
Upgrade Notes
Important changes
For security reasons eSign now rejects documents with attached documents containing embedded javascript during the document creation service.
This default feature can explicitly disabled by setting the pdf.js.reject property to false.
Also
| If you are upgrading directly from 1.9.x, check the migration steps to understand how to upgrade. |